DruvStar DataVision™
Building a zero-trust environment for your data
SaaS tool powered by AI/ML technologies providing comprehensive data observability, and unmatched insights for data governance and protection. Our clients use it for data sensitivity analysis, data access governance, and automated alerting against the compliance policies.

"Since the implementation of DataVision, we have been able to track and manage our user base and evaluate required permissions and adjust accordingly. With so many cybersecurity incidents occurring due to compromised accounts or inappropriate permissions, the level of awareness and insights has proved invaluable to us. DataVision has been a game-changer in how we understand and secure our sensitive data."

Protecting your valuable data assets is a business imperative that you can't afford to neglect.
Staying ahead of risks such as data leaks, ransomware attacks and noncompliance grows more challenging every year due to:

The complexity of your distributed and expanding IT landscape

user environment

The evolving security threats and the magnitude of cyber attacks
Cyber Incidents
#3 global risk for 2021
Cost of Cybercrime
$5 trillion estimated by 2024
Data Privacy and Security Concerns
#1 barrier to digital transformation
Organizations adopt various solutions to control unauthorized access to sensitive data — yet continue to struggle with their data governance and security.
Common data security challenges
Understanding where all the data resides across the complex and distributed ecosystem, and who touches critical data, where and how — which creates the risk of data leaks and noncompliance with governmental regulations
Staying ahead of threat actors, who are constantly evolving their tactics, looking for weaknesses to exploit — making it difficult to anticipate the next attack
Relying on disparate tools or manual processes to comply with government regulations — lacking not only assurance that authorization controls are working but also the complete picture of what data was affected and how in the event of a security incident




Gain Comprehensive Visibility and Reduce Exposure to Threats
Data Vision closes your data access visibility gaps to provide a comprehensive view of data and access through the entire lifecycle, reducing your risks of internal and external threats, improves your regulatory compliance and enables a zero trust environment — all in one, comprehensive SaaS solution

Visibility
Comprehensive 360-degree visibility into your data sources and users

Classification
A comprehensive data security map and data classification

Fully Automated Monitoring & Alerting
Policy-based data protection and monitoring

Detection
The ability to track data access and detect anomalies, regardless of source
Support for all architectures — cloud, on-premises and hybrid environments
Protect Valuable Data Assets and Reduce Risk as Your Business Grows and Your Environment Evolves
Comprehensive Data Visibility
When users access data through services or applications, do you know if they’re doing so as intended and authorized? Do you have data access assurance or is your only option to trust the vendor’s claim about the data access layer? Data Vision’s comprehensive, user-centric, 360-degree data mapping, displayed in a visually intuitive way, solves your visibility challenges by providing:
-
Automatic discovery of data and users
-
Data asset classification
-
End-to-end tracking of who/what/how of data access at all points of access and sources
- How the request to data is made.
- What data and type of data is requested.
- Who requested the data.
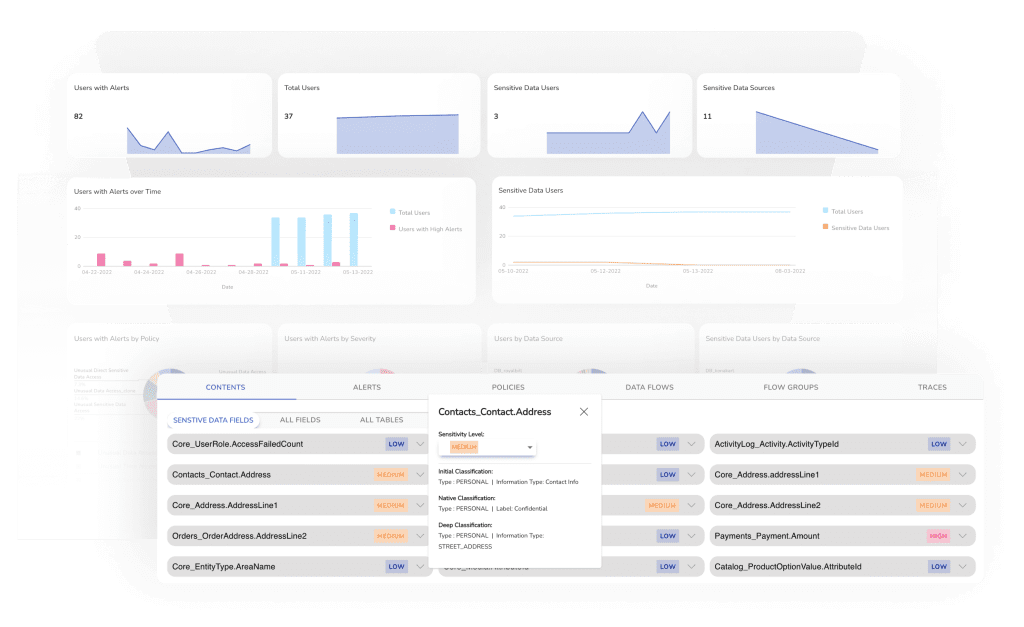
Data Vision closes visibility gaps into data sources and data access throughout the data lifecycle.
-
Discover where all your data resides across your complex, distributed ecosystem
-
Understand who touches critical data, where and how, regardless of point of access or source
-
Implement data governance and gain the context you need for protecting your data
Sophisticated Threat Detection
Threat actors are constantly surveilling your dynamic environment and changing their tactics, techniques and procedures to exploit new weaknesses and take advantage of new opportunities. Data Vision’s AI-driven anomaly detection enables you to identify threats based on behavior — so you can stay one step ahead of cyberattackers and reduce your risk.
-
Identify unusual patterns that indicate the possibility of a threat, thanks to machine learning technology that monitors services, applications and data access.
-
Detect unauthorized or abnormal access to data, defend against external and internal threats and move toward a zero-trust security model
-
Monitor activity of authorized and unauthorized users to detect emerging threats
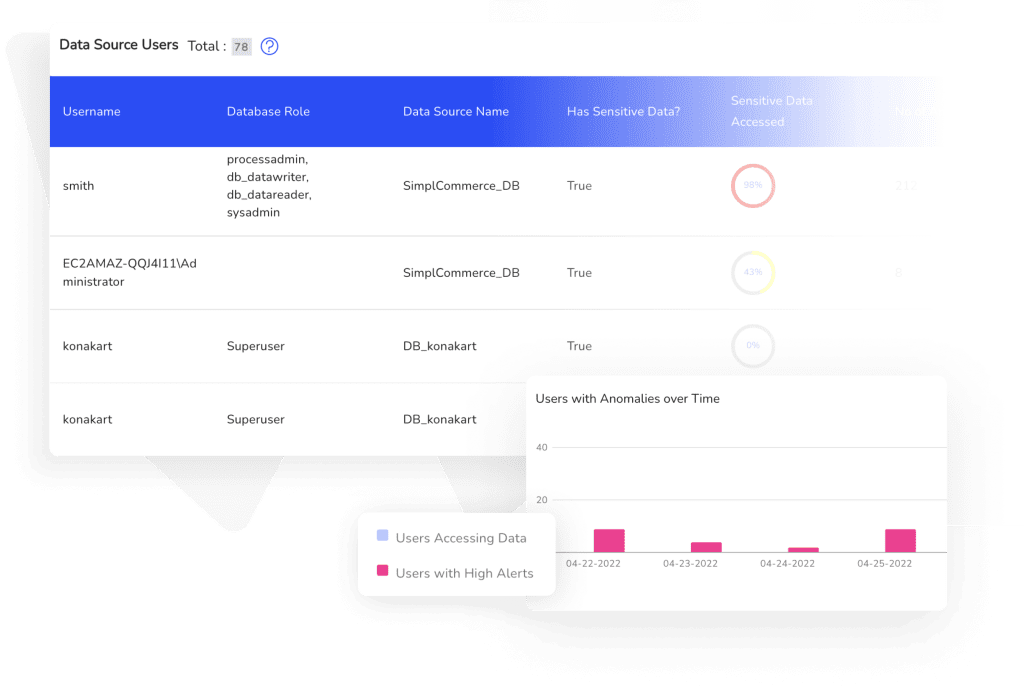
Prove that you meet the regulatory requirements for data violations
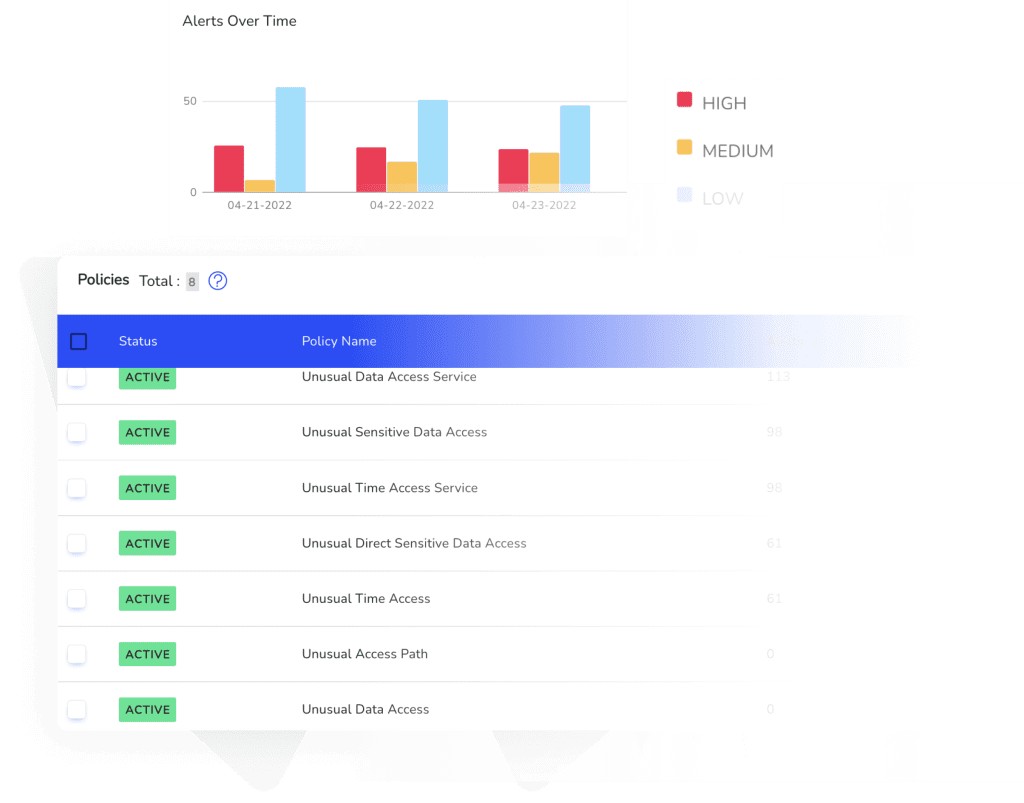
Robust Policy Enforcement
Data protection policies by themselves may not be enough to comply with government regulations because you’re relying on the vendor’s assurance that your authorization controls are working. Data Vision reduces your risk, secures your data and simplifies compliance by monitoring your environment for policy violations while facilitating investigations into anomalous events.
-
Monitor user behavior and compliance with a continuous detection and compliance-ready dashboard that provides a high-level view of data to monitor compliance
-
Quickly implement data access policies that comply with regulations such as HIPAA, GDPR, CCPA and PCI-DS.
-
Automated alerts on abnormal activities or access to sensitive data and conduct investigation drill-downs so you can take fast actions to protect your data assets.
Data Vision Capabilities
View data assets
View authorized users
Provide alerting on anomalous access
Provision and deprovision access
Monitor access
Visualize data classification
Manage and escalate alerts and receive notifications
Track and show data owners and custodians
Classify your data automatically
Notifications
Track access expiration

- November 11, 2021

A Critical CCPA Compliance Step Your Organization May Be Missing

- October 19, 2021

[White Paper] Closing data visibility gaps in your complex, distributed environment

- September 28, 2021

Defending Against Data Breaches with Zero Trust Security

Enhancing Indian Head Casino’s Data Security and Threat Detection with DruvStar’s DataVision
Leveraging the sophisticated anomaly detection feature of DataVision, the casino could effectively identify sensitive irregularities, significantly strengthening their threat detection capabilities.

Sports betting company protecting against cyber attacks
Pointsbet partnered with DruvStar and successfully stopped repeated cyber-attacks without growing their internal resources.

Comprehensive Cybersecurity assessment in under a week
Seven feathers partnered with DruvStar and got a comprehensive cybersecurity assessment in under a week with minimal impact on day to day operations.
Protect your data with DruvStar DataVision™
DruvStar DataVision™ enables building a zero-trust environment for data in an enterprise. It’s a SaaS tool powered by AI/ML technologies and provides comprehensive data observability, and unmatched insights for data governance and protection. Our clients use it for data sensitivity analysis, data access governance, and automated alerting against the compliance policies.










