Defending Businesses from Dangerous Cyber Threats
Services include Managed Detection and Response, Data Protection, Vulnerability Assessment, and Penetration Testing.

Since the implementation of DataVision, we have been able to track and manage our user base and evaluate required permissions and adjust accordingly. With so many cybersecurity incidents occurring due to compromised accounts or inappropriate permissions, the level of awareness and insights has proved invaluable to us. DataVision has been a game-changer in how we understand and secure our sensitive data.

Nathan Whitney
Director of Information Technology Indian Head Casino


DruvStar and Kindbridge Announce New Strategic Partnership to secure Kindbridge Healthcare Platform.
The partnership between the two companies includes assistance in both software development and live operations to ensure that Kindbridge can offer a secure and safe platform.
Meet Nevada's New Cybersecurity Regulation 5: Advanced Cybersecurity Solutions for Nevada Gaming Operators
DruvStar specializes in risk assessment, threat monitoring, data security and compliance. With our expertise, you can stay ahead of the game and meet the requirements set forth by the Nevada Gaming Control Board.
Enhancing Indian Head Casino's Data Security and Threat Detection with DruvStar's DataVision
Leveraging the sophisticated anomaly detection feature of DataVision,
the casino could effectively identify sensitive irregularities, significantly
strengthening their threat detection capabilities.
DruvStar Governor - vCISO and vCSM Services
- Incidence Response Preparation
- Risk Management
- Business Continuity Planning
- Cybersecurity Governance
- Rapid Incidence Response and Recovery




Awards and Partnerships
Recipient of the 2021 Gaming and Leisure Partner of the Year Award, recognizing DruvStar for unprecedented commitment to customer cybersecurity, and dedication to the gaming industry.





Solutions you can trust
Cyberthreats are increasingly menacing and a distraction for executives. Having DruvStar on board ensures cyber safety and allow clients to focus on business.
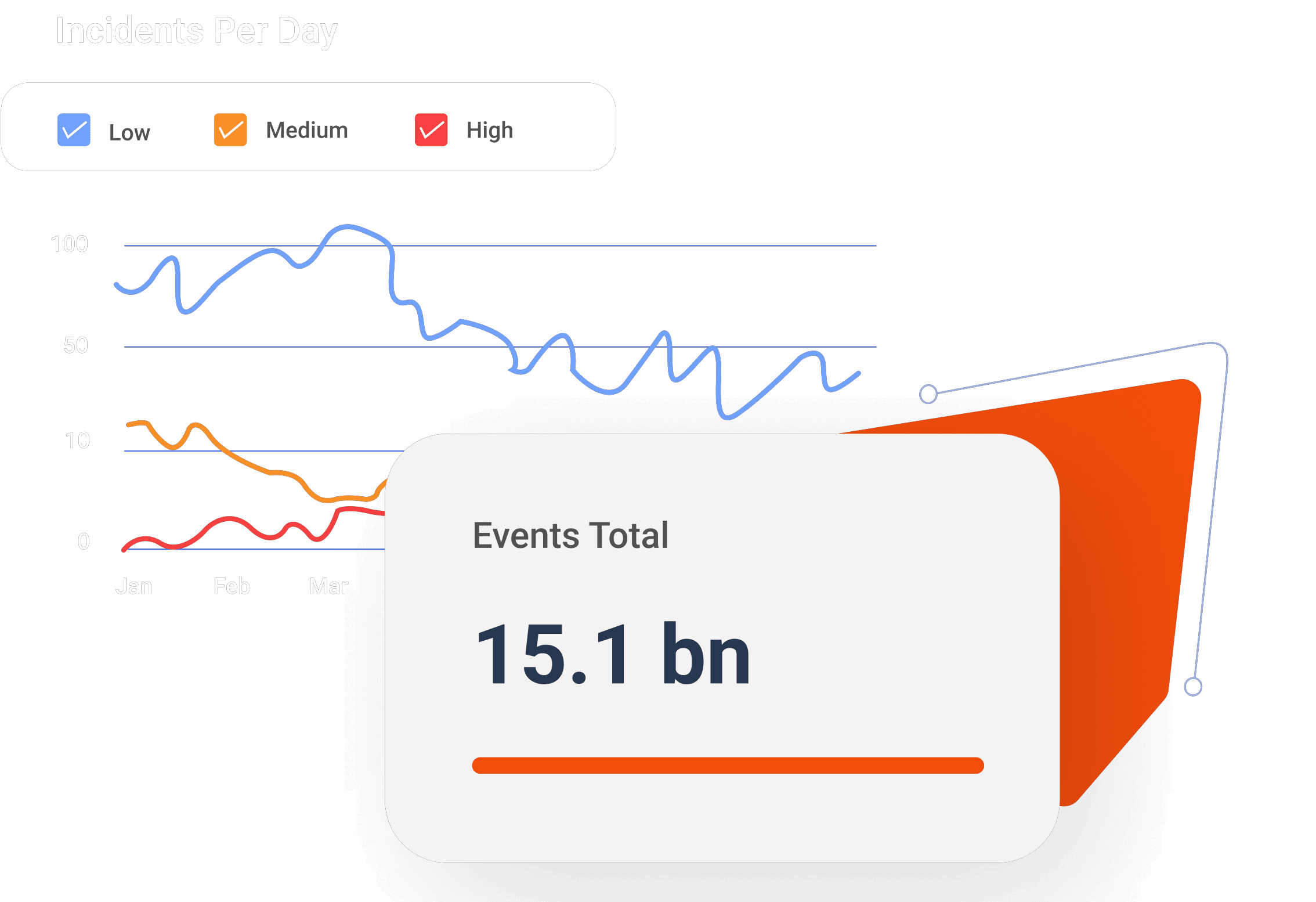

Single Point-In-Time Assessments
Our Cybersecurity Assessment Services addresses regulatory requirements for carrying out risk assessments. Our team of cybersecurity experts conducts thorough assessments of our clients' systems, identifying and closing the vulnerabilities that attackers use to infiltrate their systems. This is critical for ensuring compliance with regulations, which require either annual or quarterly assessments, and protecting against potential cyber threats.

Data Safety and Governance
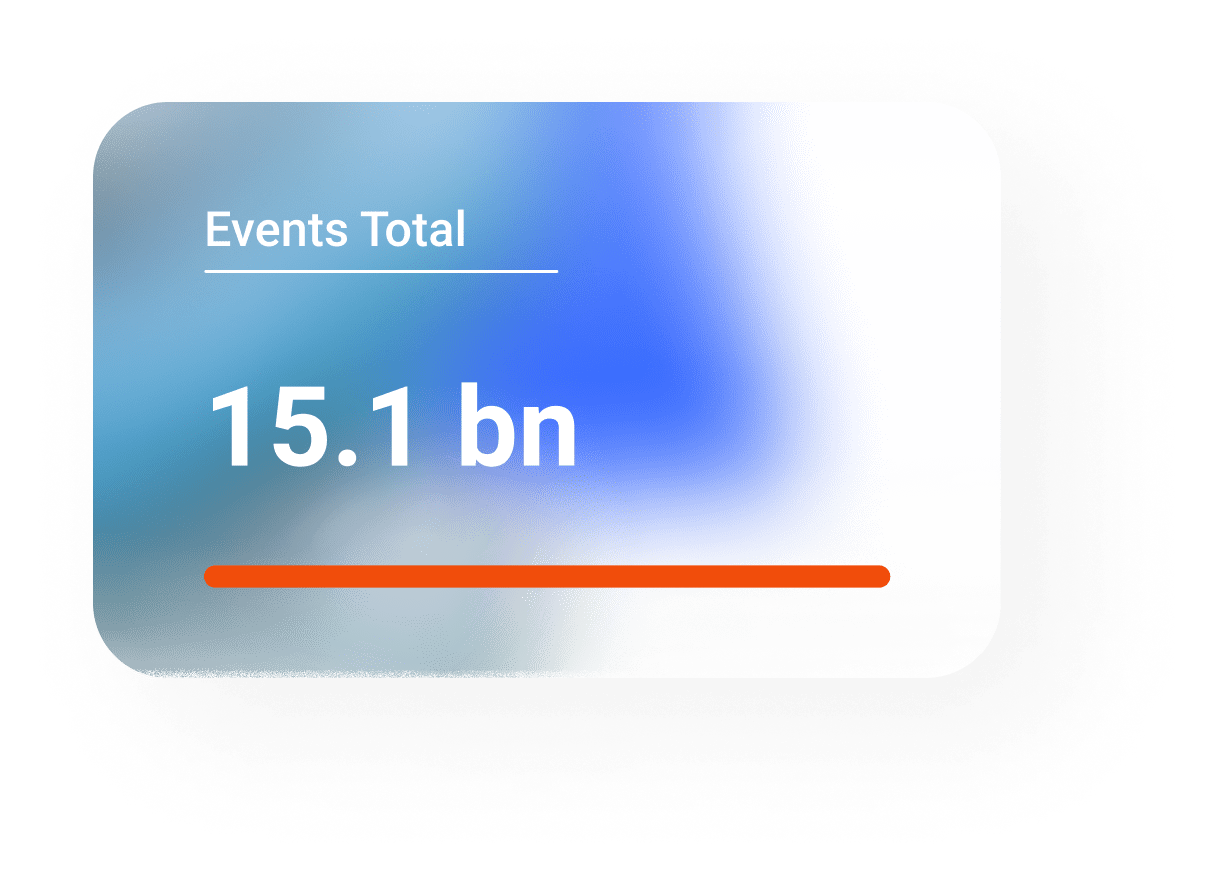
Our patented DataVision platform provides Data Safety with observability and intelligence functions. It is a cloud-native, AI/ML-based data security and compliance product that provides powerful insights into data flow and automatically flags data policy violations. It also helps meet the regulatory audit and compliance requirements in data safety and privacy. Helps comply with GDPR, CCPA, ISO, SOC2, and other data protection standards.
Continous 24x7 Safety
DruvStar Threat Insights™ is an AI based advanced technology solution, which provides Managed Detection and Response (MDR) SaaS, for real-time threat detection and incidence response. Our team of security experts utilizes external threat intelligence and continuous monitoring of networks, endpoints, users, on-premises, and cloud environments for signs of malicious activity and prepares our clients to improve their cyber-security posture in an informed way.






Enhancing Indian Head Casino’s Data Security and Threat Detection with DruvStar’s DataVision
Leveraging the sophisticated anomaly detection feature of DataVision, the casino could effectively identify sensitive irregularities, significantly strengthening their threat detection capabilities.

Sports betting company protecting against cyber attacks
Pointsbet partnered with DruvStar and successfully stopped repeated cyber-attacks without growing their internal resources.

Comprehensive Cybersecurity assessment in under a week
Seven feathers partnered with DruvStar and got a comprehensive cybersecurity assessment in under a week with minimal impact on day to day operations.
Eliminate Cyber Risk With DruvStar
We’re here to help. Reach out to schedule an introductory call and learn more about how DruvStar can benefit your organization.