Premium security services for healthcare
Safeguarding PHI is critical for Healthcare providers to provide quality patient care, while also meeting ever growing HIPAA compliance requirements.
DruvStar is a trusted cybersecurity provider for the healthcare industry. We understand the complex IT landscape and the security threats that come with it. We provide targeted security solutions that help meet HIPAA compliance requirements and keep your patients’ data safe.






The New Healthcare Tech Boom
There has been a recent explosion in new healthcare technologies: from wearable monitoring devices to cloud collection and analytics services, and the movement of patient data to cloud services.
This is driving an ever-increasing proliferation of technologies throughout medical facilities, all needing to communicate safely and securely to their target infrastructures.
These challenges are moving at the speed of light, and with limited resources IT teams struggle to keep up. At the same time, the industry is becoming a lucrative target for cyber-criminals.
According to the IBM Cost of Data Breach report, average cost per data breach continued to grow for the healthcare industry in 2021 to a staggering $9.23 Million. This is considerably higher than any other business sector.
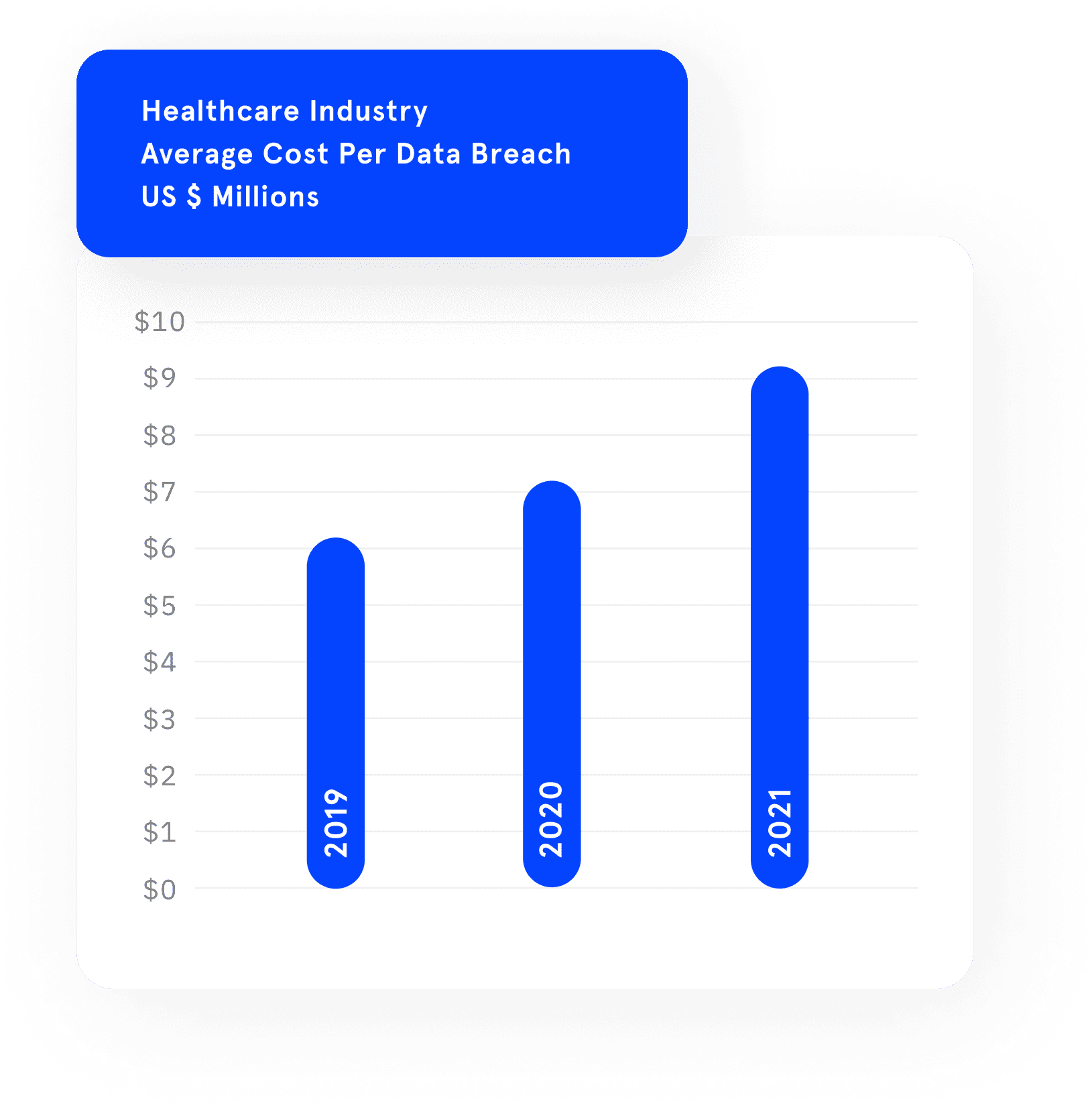
DruvStar's services greatly reduce the risk of successful attacks across new technologies and complex IT infrastructures.
Solutions you can trust
Cyberthreats are increasingly menacing and a distraction for executives. Having DruvStar on board ensures cyber safety and allow clients to focus on business.

Single Point-In-Time Assessments
Our Cybersecurity Assessment Services addresses regulatory requirements for carrying out risk assessments. Our team of cybersecurity experts conducts thorough assessments of our clients' systems, identifying and closing the vulnerabilities that attackers use to infiltrate their systems. This is critical for ensuring compliance with regulations, which require either annual or quarterly assessments, and protecting against potential cyber threats.

Data Safety and Governance
Our patented DataVision platform provides Data Safety with observability and intelligence functions. It is a cloud-native, AI/ML-based data security and compliance product that provides powerful insights into data flow and automatically flags data policy violations. It also helps meet the regulatory audit and compliance requirements in data safety and privacy. Helps comply with GDPR, CCPA, ISO, SOC2, and other data protection standards.
Continous 24x7 Safety
DruvStar Threat Insights™ is an AI based advanced technology solution, which provides Managed Detection and Response (MDR) SaaS, for real-time threat detection and incidence response. Our team of security experts utilizes external threat intelligence and continuous monitoring of networks, endpoints, users, on-premises, and cloud environments for signs of malicious activity and prepares our clients to improve their cyber-security posture in an informed way.
Product Security Validation
DruvStar’s experienced testers execute security validation against a broad array of medical devices, gateways, and back-end services to help ensure that patient data remains private and free from modification.
Our testers seek out vulnerabilities by looking for security gaps in Bluetooth, Wi-Fi, encryption, authentication. validation, data storage, APIs, web applications, and many more. Device and service vendors can greatly reduce the risk of attack via their product offerings

Internal Penetration Testing
-
If a bad actor plugs into your network, what can they achieve?
-
If an employee gets caught out by a phishing attempt, what’s the impact?
-
What’s running in your environment, and is it safe according to current industry standards?
-
How safe is your Wi-Fi network?
Answer these and many other questions with an internal penetration test and vulnerability scan. DruvStar’s team of ethical hackers will work through hundreds of attack scenarios to provide critical insights and guidance to tighten and protect your network.
External Penetration Testing
Attackers can identify and target a vulnerable system from their couch.
Understand the access that can be gained from the outside world to your infrastructure.
Know that the services that you expose are safe.
DruvStar's Threat Insights™
Detection and Response is a critical component of any mature security solution.
While ransomware can hit quickly, threats often lurk in systems for extended periods, gathering as much information as possible. Picking up data on your customers and employees and looking for opportunities to escalate their capabilities.
-
Are your environments continually monitored for bad actors and actions?
-
What are you doing for detection?
-
How many events are being captured and handled for you?
-
When someone opens a phishing email, how quickly is this detected?
-
Do you know when you’re under attack?
DruvStar’s Security Operations team continually monitors for bad actors and persistent threats and works closely with your team to respond at the moment it’s needed, providing continuous coverage, every single day.
DruvStar Swat Team
You’ve run penetration tests,. You’ve closed the identified vulnerabilities. You’re running antivirus.
Now what are you doing differently to ensure that you’re safe?
DruvStar’s D-SWAT rapidly deploys a Managed SOC to your environment with real threat hunters on-site. This engagement weeds out active attackers, discovers signs of compromise, and uncovers live flaws in action using up to the minute threat hunting.
D-SWAT identifies and roots out cyber attackers that are already lurking inside your system.

You can also come and visit us in person at

HIMSS 2022 – March 14-18 – Orange County Convention Center, Orlando FL – Booth 300-03

Enhancing Indian Head Casino’s Data Security and Threat Detection with DruvStar’s DataVision
Leveraging the sophisticated anomaly detection feature of DataVision, the casino could effectively identify sensitive irregularities, significantly strengthening their threat detection capabilities.

[Ebook] Cyber Attack Emulation : An Essential Tool for Strengthening Your Defenses
Cyber attacks are a major concern for organizations of all sizes due to the ever-growing dependence on technology and the internet. To be prepared for any potential cyber threats, businesses should use a human-implemented cyber attack emulation as a proactive measure. The primary objective of such emulations are to assess the organization’s ability to detect, respond to, and recover from a cyber attack.
MDR

Healthcare Managed Detection and Response (MDR)
Healthcare leaders rank #1 at $9.23M on the list of the average cost of a data breach, based on IBM’s 2021 Cost of a data breach report.
Being at the center of attention for….
Download PDF
Eliminate Cyber Risk With DruvStar
We’re here to help. Reach out to schedule an introductory call and learn more about how DruvStar can benefit your organization.







